February 7, 2021
Traffic filtering is a method of identifying and prioritizing different traffic types passing through a common router by applying filter rules based on your network requirements. When using MikroTik RouterOS, there are several ways to achieve this. One of the most common techniques is to apply traffic limitations by making use of IP Address Lists.
Traffic Filter on Source or Destination IP Addresses
Traffic can either be filtered by source, or destination IP addresses. If you want to filter specific users on your LAN, this can be achieved by using source addresses. Any traffic leaving the LAN (Internet) will be classified with destination addresses. A combination of these and other settings can also be used to achieve more specific results, depending on your requirements.Blocking Traffic to Specific Websites
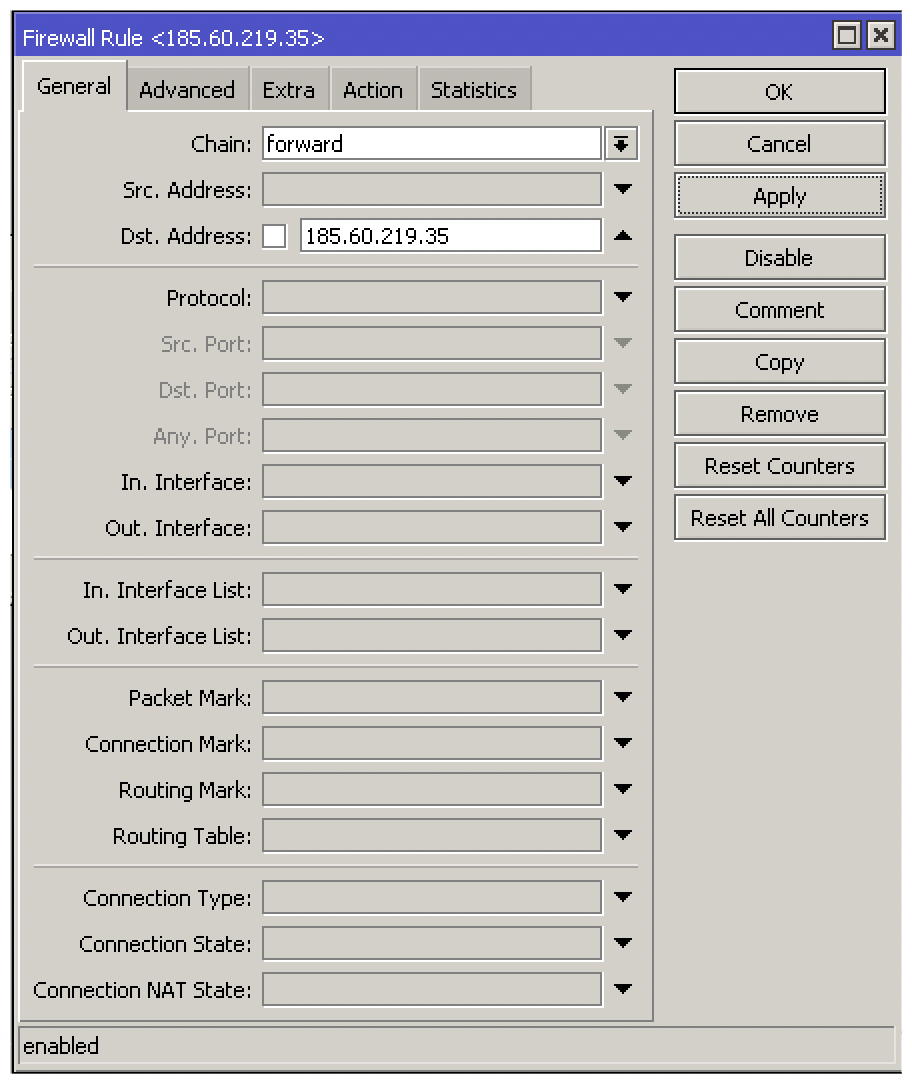
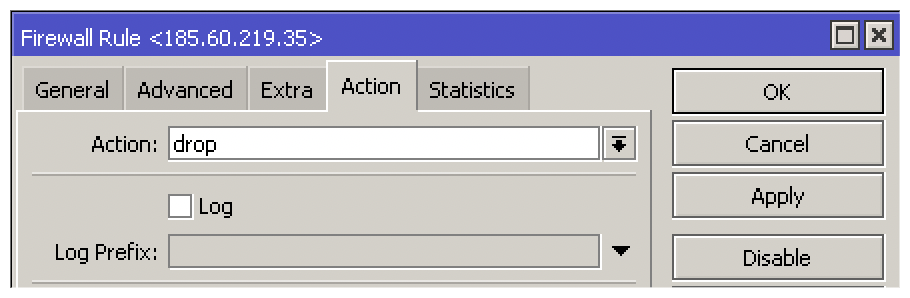
One of the most common questions we are asked by new MikroTik users is 'How do I block websites?'. In our example, we will block all traffic going to Facebook.In a perfect world, Facebook would have only a single IP address and we could configure one simple rule. If this were the case, we could configure any destination IP address of facebook.com to be dropped. In the MIkroTik firewall filter, the Forward chain should be used to capture all traffic passing through the router. Here is an example of what that configuration would have looked like.
Firewall Filter
CLI Example
/ip firewall filter
add action=drop chain=forward dst-address=185.60.219.35
The problem with the above is that Facebook uses multiple IP addresses for access to its servers globally. Therefore, the above would not be very effective. One possible solution would be to figure out which IP addresses are being used and then add multiple filter rules to accomplish this, however, doing this would use unnecessary resources on the router which is neither scalable nor practical. A better solution would be to generate an Address List of all the associated IP's and create a single rule to filter them.
Generate a MikroTik Address List
You can create individual entries using specific IP's, IP ranges or DNS host names.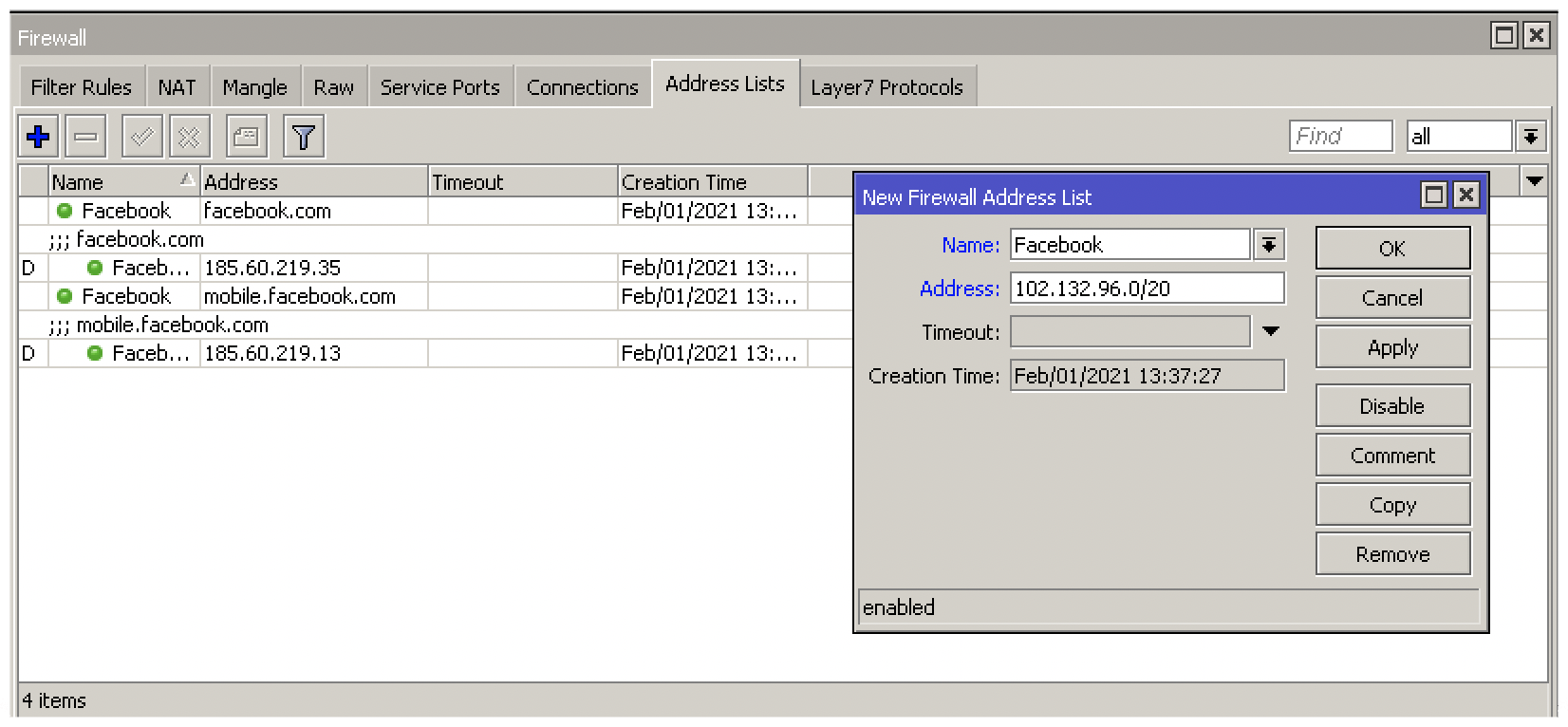
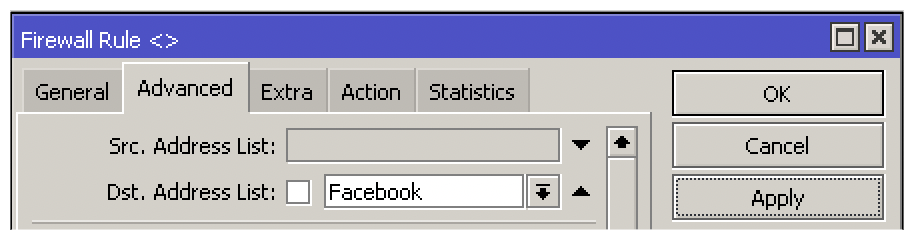
Use the list instead of the dst-address field in your firewall filter rule in the Advanced tab.
CLI Example
/ip firewall address-list
add address=185.60.219.35 list=Facebook
add address=mobile.facebook.com list=Facebook
add address=102.132.96.0/20 list=Facebook
/ip firewall filter
add action=drop chain=forward dst-address-list=Facebook
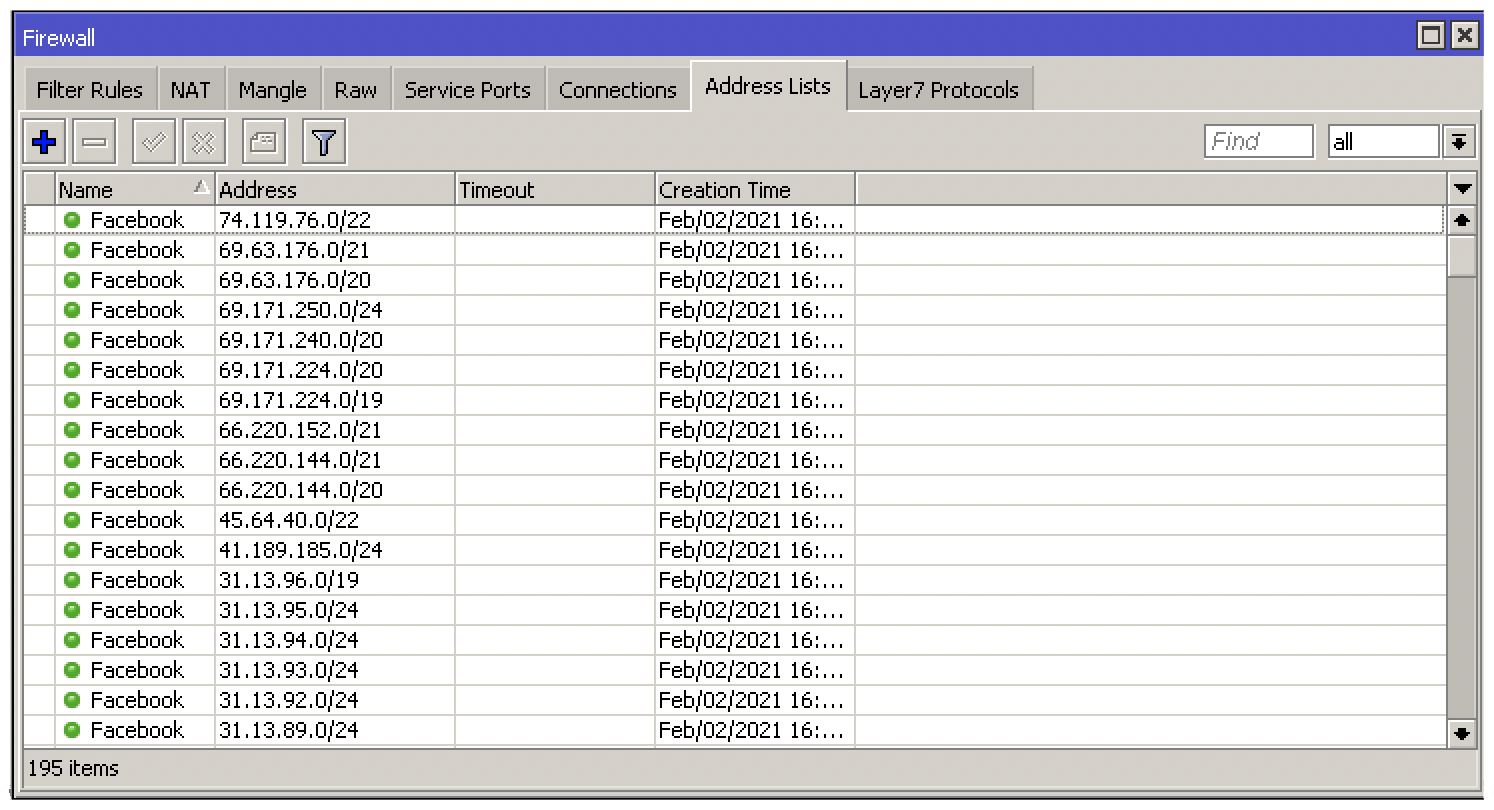
Creating Large Address Lists
Adding individual entries for smaller sites is great but Facebook has thousands of IP addresses. To overcome this issue you would need to create your own lists and import them into the router. In order to get updated information you can use this BGP toolkit.Here you will be able to search all IP addresses from various servers updated on a regular basis. These IP addresses can simply be copied into a document which can be uploaded to the router later on.
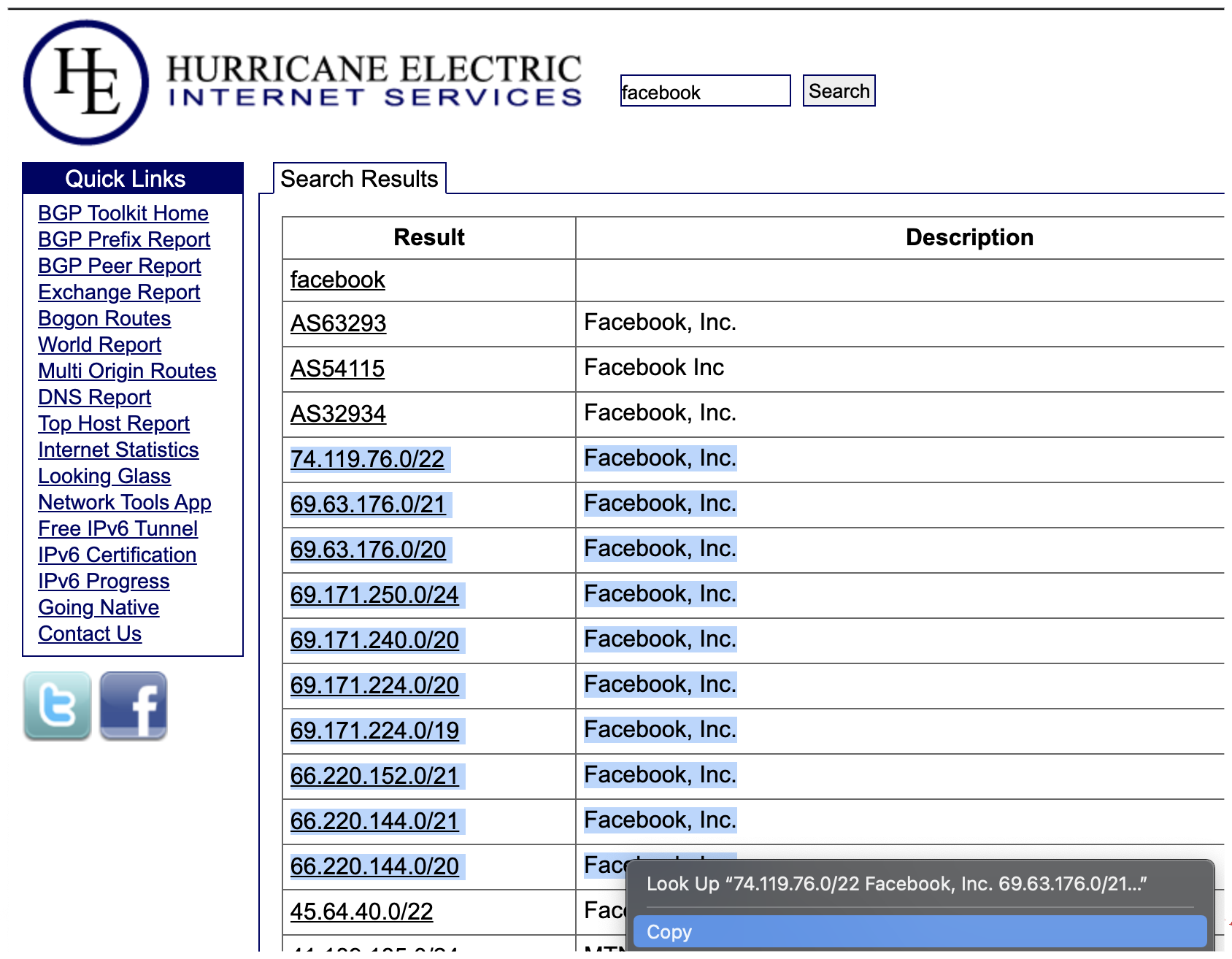
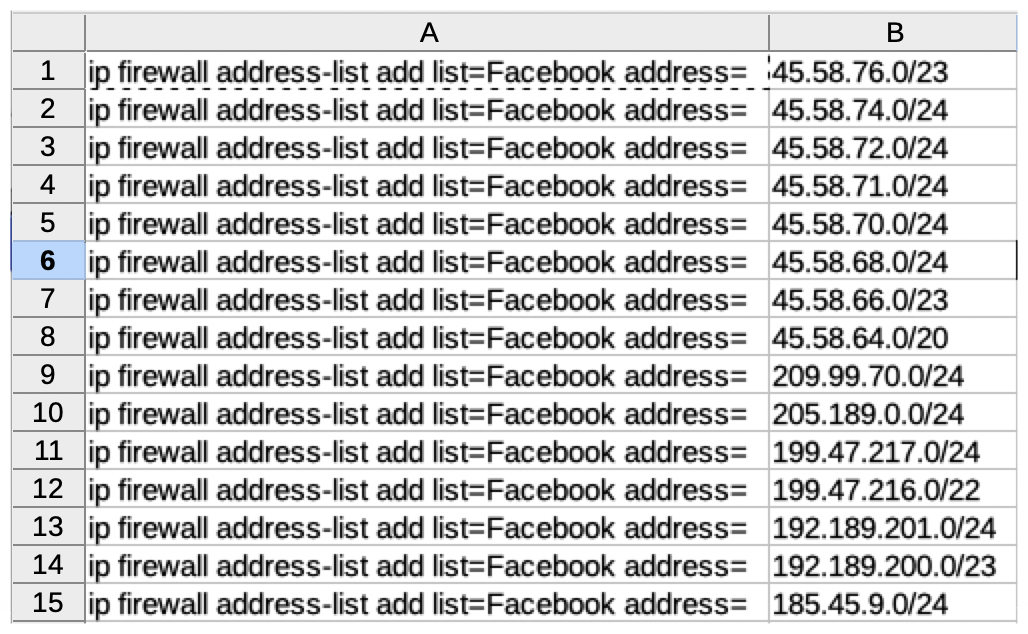
To prepare this information for MikroTik, you will need to make a spreadsheet with a column for the IP addresses you copied while leaving a separate column for the command used to create the address list on the router. To do this, you need to use the CLI syntax as if you were adding addresses using the RouterOS CLI.
Command: ip firewall address-list add list=Facebook address=
Once you have copied, pasted and removed any irrelevant information. Your spreadsheet should look like this:
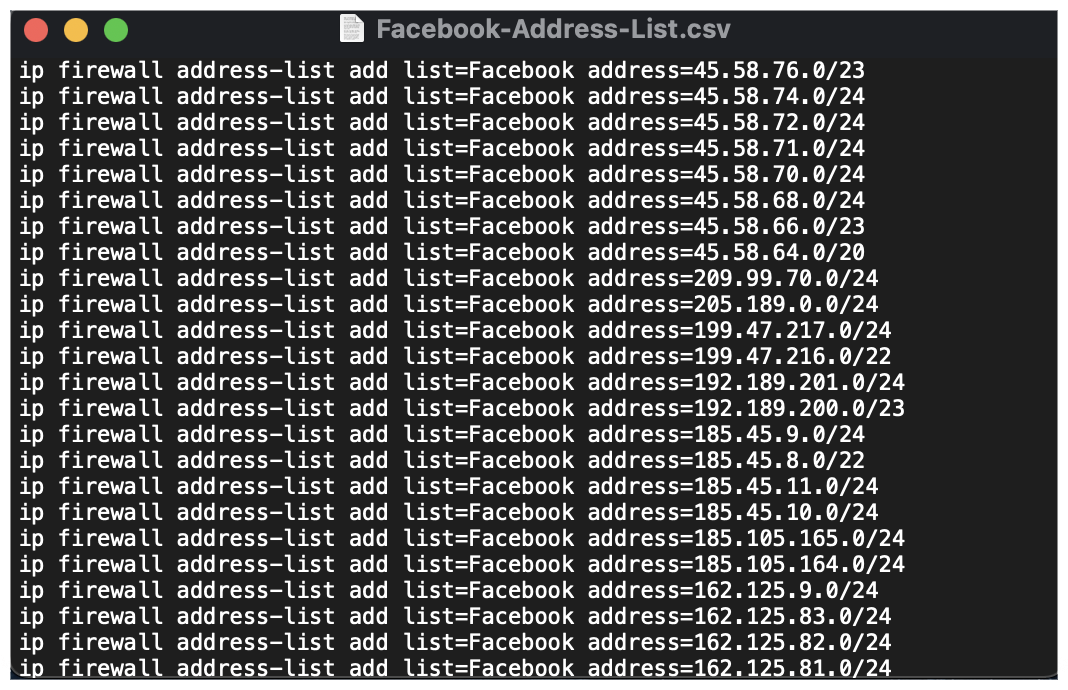
Next, you will need to convert your spreadsheet to unformatted text. Either export as CSV file or copy paste into a notepad editor. When using CSV, verify delimiter options to maintain the correct syntax to prevent errors when uploading your configuration.
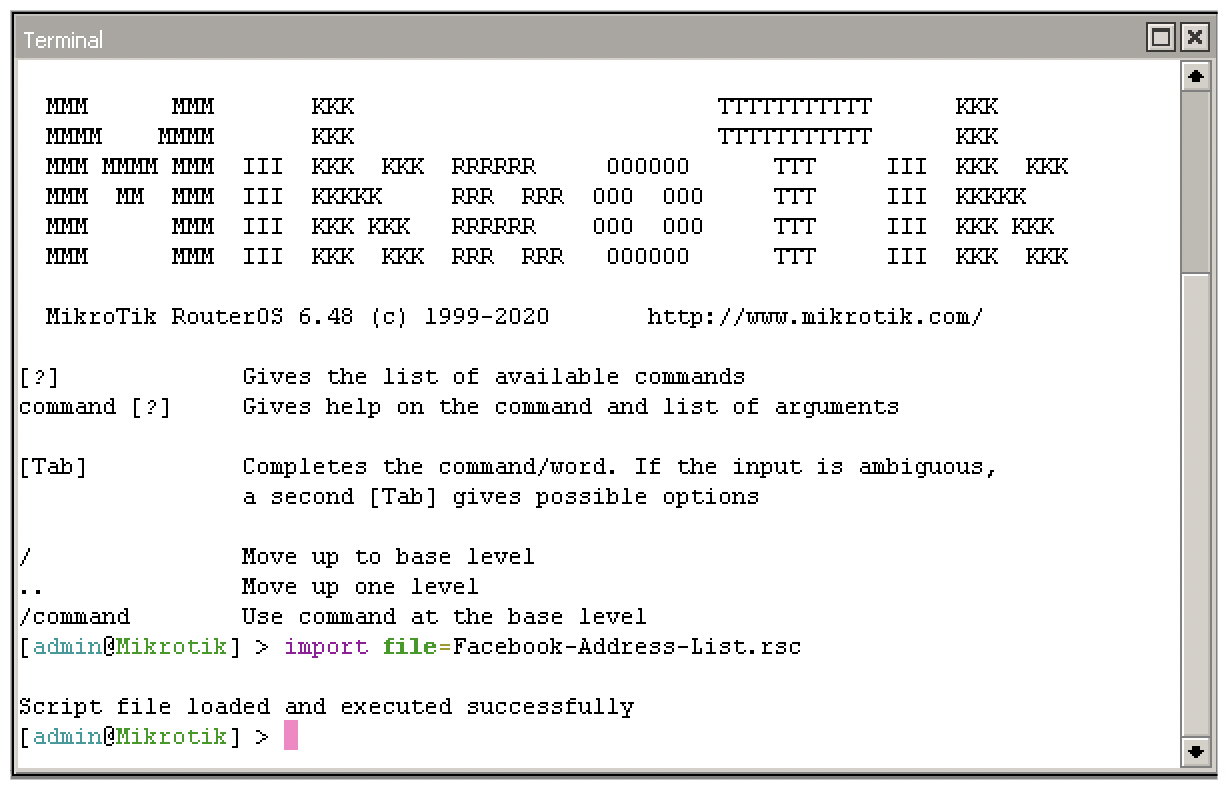
Simply copy and paste your unformatted text into a new terminal or save in RSC format and import the script file via terminal (Make sure you have copied the file into the files list first). You can verify the new entries in the Address List menu of the firewall.
Command: import file=name_of_your_file.rsc
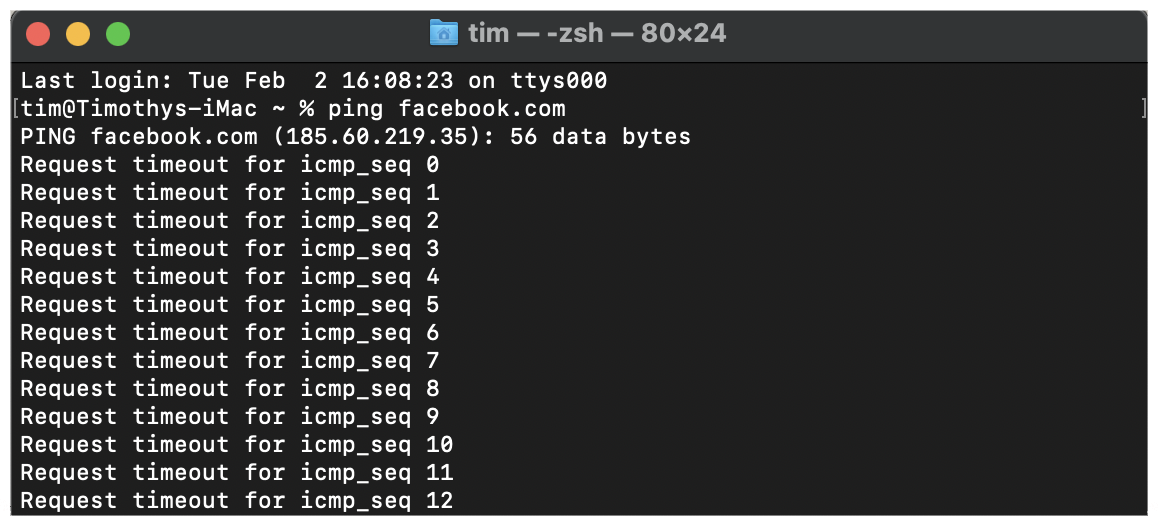
You can test the configuration and monitor the byte counter to confirm everything is working
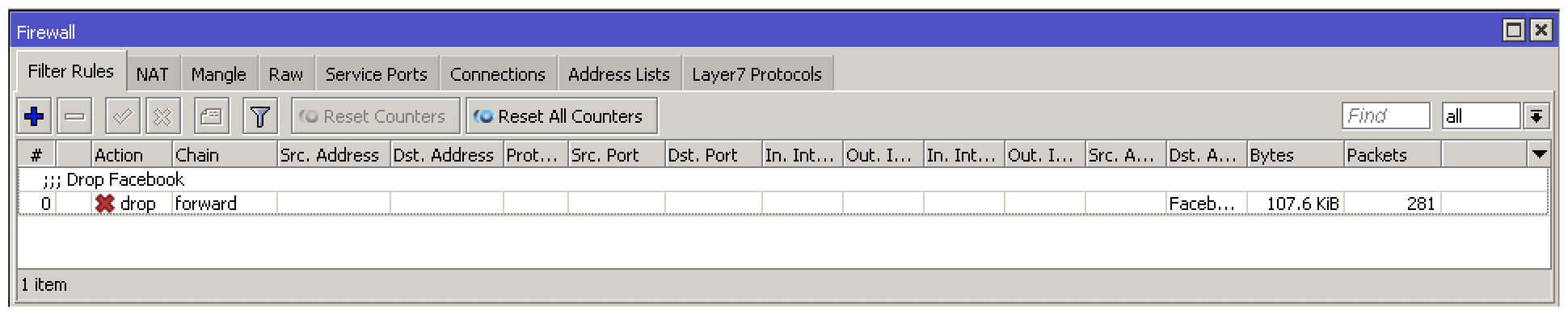
Making use of address lists is simple yet effective, and it's not limited to just blocking websites. There are many applications where this technique could be applied for filtering or QoS which is why it is so widely used in RouterOS.








